Karios Native Disaster Recovery Solutions

Karios Native Disaster Recovery Solutions
Karios delivers a fully integrated Disaster Recovery (DR) solution built directly into its hyperconverged infrastructure—eliminating the need for external backup tools or complex orchestration. It unifies distributed storage, encryption, verification, and instant recovery into a self-healing, cyber-resilient platform.
At its foundation, Karios uses SeaweedFS, a distributed object-storage layer that ensures continuous data availability and scalability across geographically separated sites. Data is automatically replicated, verified with cryptographic checksums, and instantly recoverable, guaranteeing integrity and uptime under any conditions.
Through a secure client-server model, backups are performed incrementally with AES-256-GCM client-side encryption, ensuring complete confidentiality even if infrastructure is compromised. Role-based access control and integration with Active Directory, OpenID, and PAM enforce enterprise-grade authentication and least-privilege access. Every data block and manifest is validated using SHA-256 checksums to detect corruption, tampering, or bit rot before recovery.
Karios is inherently ransomware-resistant. Immutable, write-once-read-many (WORM) backups prevent deletion or modification—even by administrators. Entropy-based anomaly detection identifies abnormal encryption activity, while air-gapped replication and delayed synchronization preserve clean recovery points across remote sites.

When disaster strikes, recovery is instantaneous. Full virtual machines or individual files can be restored in seconds through the web interface, or booted directly from backup snapshots via live-restore, allowing operations to resume immediately while full restoration completes in the background. Incremental, deduplicated backups minimize bandwidth and storage use while maintaining rapid recovery readiness.
Built-in integrity verification and cryptographic deduplication provide up to 95% storage efficiency and automatic corruption isolation. Administrators can schedule automated verification scans to continuously validate data health with minimal performance impact.
For compliance and testing, Karios supports cleanroom recovery secure, isolated environments that allow organizations to verify backup validity and measure Recovery Point (RPO) and Recovery Time Objectives (RTO) without affecting production systems. Air-gapped recovery ensures backup safety even in compromised networks.
By merging distributed storage, AI-driven automation, and integrated cyber protection, Karios redefines disaster recovery as an intelligent, autonomous service. It provides seamless resilience for private, hybrid, and edge environments ensuring data remains protected, verifiable, and instantly recoverable whenever disruption occurs.
In Detail:
1. Core Architecture: Distributed Storage Foundation
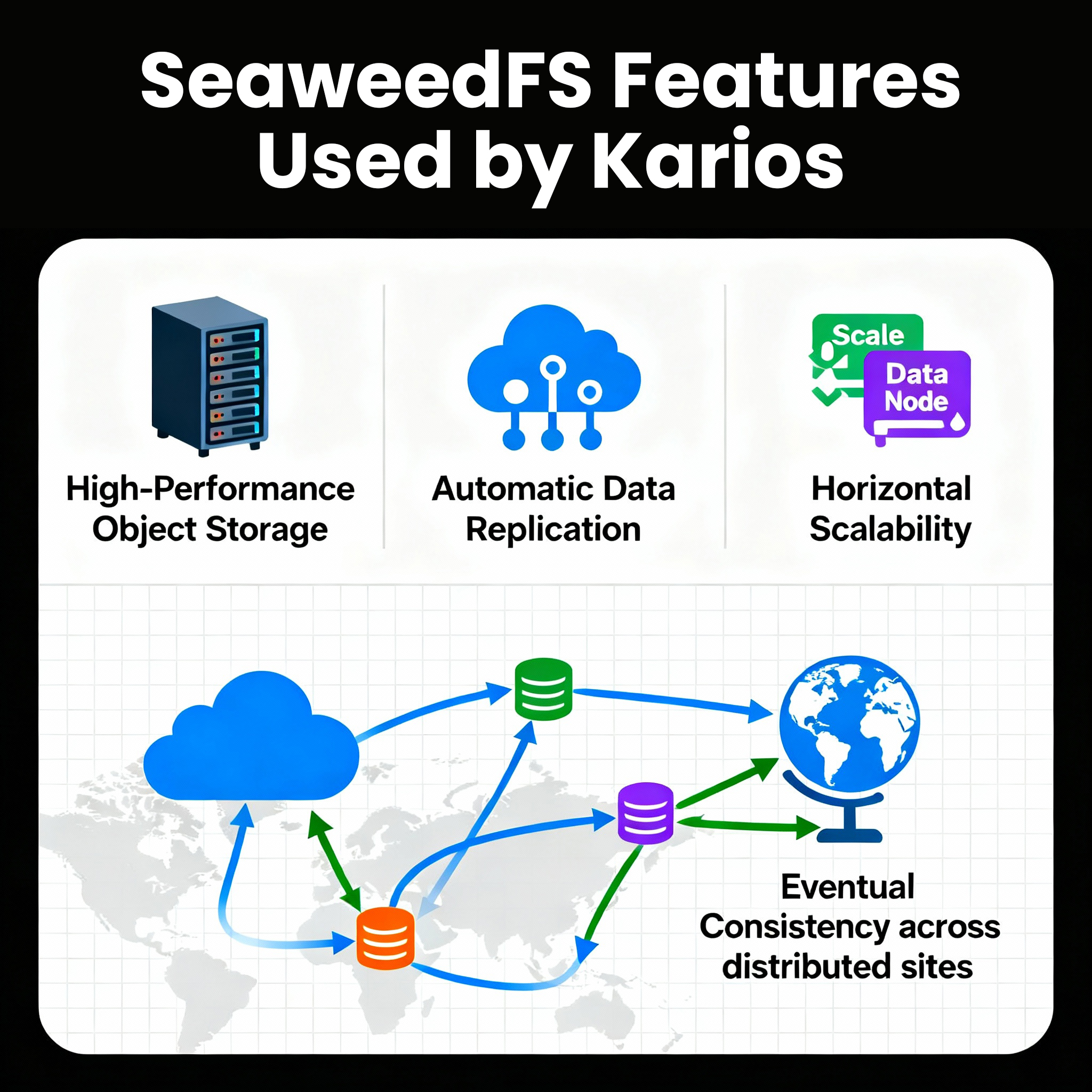
Kairos employs SeaweedFS as one of its foundational storage layer, providing a highly scalable, object-storage infrastructure that ensures data availability, integrity, and resilience across geographically distributed sites. SeaweedFS delivers:
- High-Performance Object Storage: Optimized for both small and large file operations with minimal latency
- Automatic Data Replication: Configurable replication policies ensure data redundancy across multiple nodes and geographic locations
- Horizontal Scalability: Seamless capacity expansion without service interruption
- Eventual Consistency Model: Guarantees data synchronization across distributed infrastructure
2. Client-Server Model
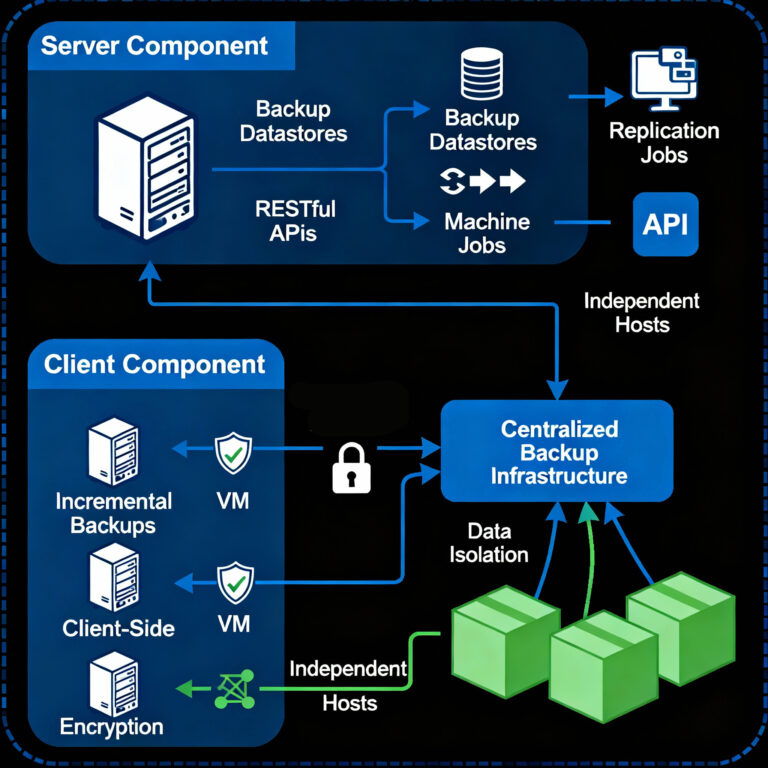
The disaster recovery solution utilizes a client-server architecture wherein:
- Server Component: Manages backup datastores, coordinates replication jobs, and exposes RESTful APIs for integration
- Client Component: Executes on protected virtual machine hosts, performing incremental backups with client-side encryption before transmission
- Separation of Concerns: Multiple independent hosts can utilize centralized backup infrastructure while maintaining data isolation.
3. Cyber Protection Against Ransomware and Malware
Multi-Layered Defense Strategy
Kairos implements comprehensive ransomware protection through several integrated mechanisms that efficiently respond to cyber incidents:
Client-Side Authenticated Encryption
All backup data is encrypted on the client-side using AES-256 in Galois/Counter Mode (GCM) before transmission to the backup server. This ensures that data remains secure and useless to unauthorized users, even if the backup infrastructure is compromised. Encryption keys are managed through a hierarchical key management system, with master keys generated as RSA public/private key pairs for secure key recovery.
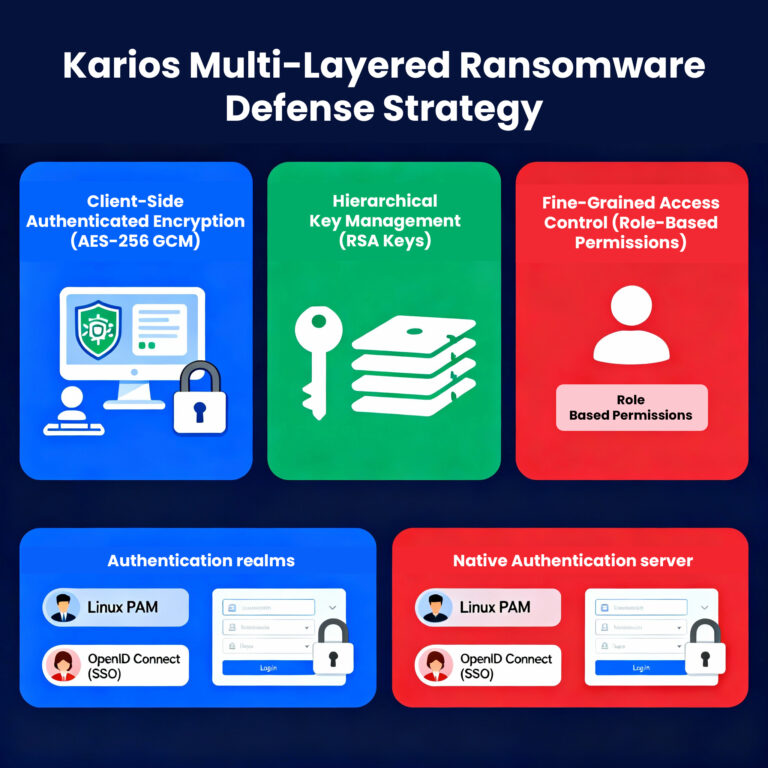
Fine-Grained Access Control
The platform enforces role-based access control (RBAC) with granular permissions, ensuring users are restricted to only the access levels required for their functions. Authentication is supported through multiple realms:
- Linux PAM: Integration with system-level user authentication and Active Directory
- OpenID Connect: Enterprise single sign-on capabilities
- Native Authentication Server: Purpose-built authentication for backup operations with comprehensive permission management
Fine-Grained Access Control
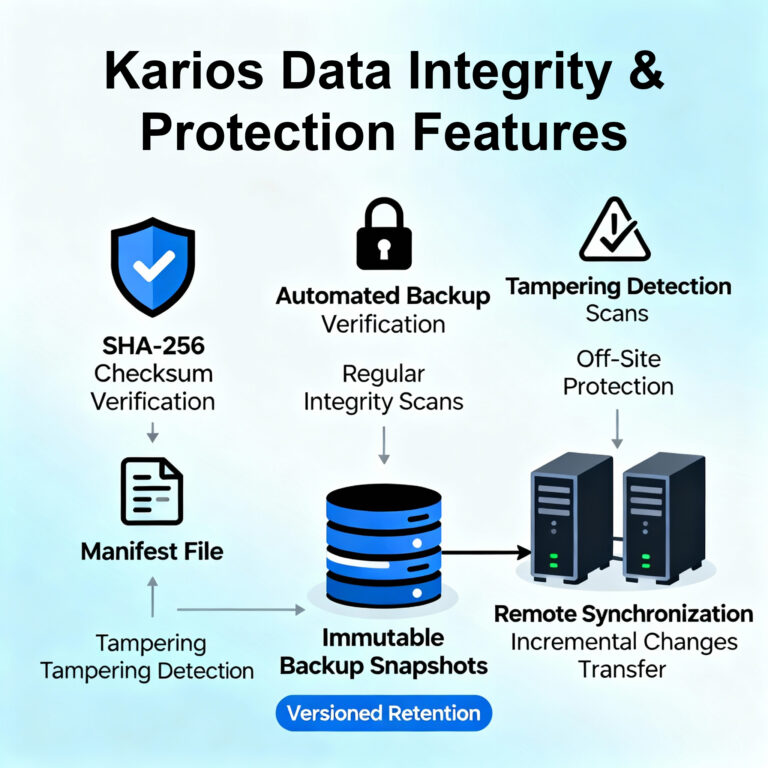
Data Integrity Verification
A built-in SHA-256 checksum algorithm ensures accuracy and consistency of all backup data. Within each backup operation, a manifest file containing checksums for all backup components is generated, enabling:
- Automated backup verification to detect data corruption or bit rot
- Regular integrity scanning on scheduled intervals
- Detection of tampering or unauthorized modifications
Immutable Backup Snapshots
Backup snapshots are stored in an immutable format, preventing modification or deletion by malicious actors. This immutability, combined with versioned retention policies, ensures that clean recovery points remain available even in the event of a successful ransomware attack.
Off-Site Protection Through Remote Synchronization
The platform enables efficient synchronization of datastores to geographically remote locations for enhanced redundancy. Only incremental changes since the previous synchronization are transferred, minimizing network bandwidth requirements while maintaining comprehensive off-site disaster recovery capabilities.
4. Fast and Reliable VM Recovery
Lightning-Fast Restoration Capabilities
Kairos prioritizes recovery speed, accuracy, and flexibility, recognizing that recovery operations must be frictionless and minimize administrative burden.
Rapid Full VM Recovery
When disaster strikes, complete virtual machines can be restored in seconds through the intuitive web-based interface. The streamlined recovery process eliminates unnecessary complexity and reduces the time required to return services to operational status.
Granular Recovery Options
Rather than requiring full restoration when only specific data is needed, Kairos provides:
- Single File/Directory Recovery: Extract individual files or directories from VM backups without full restoration
- Interactive Recovery Shell: Command-line interface for precise, file-level recovery operations
- Snapshot Catalog Navigation: Quickly search backup archives to locate specific content and restore single objects instantly
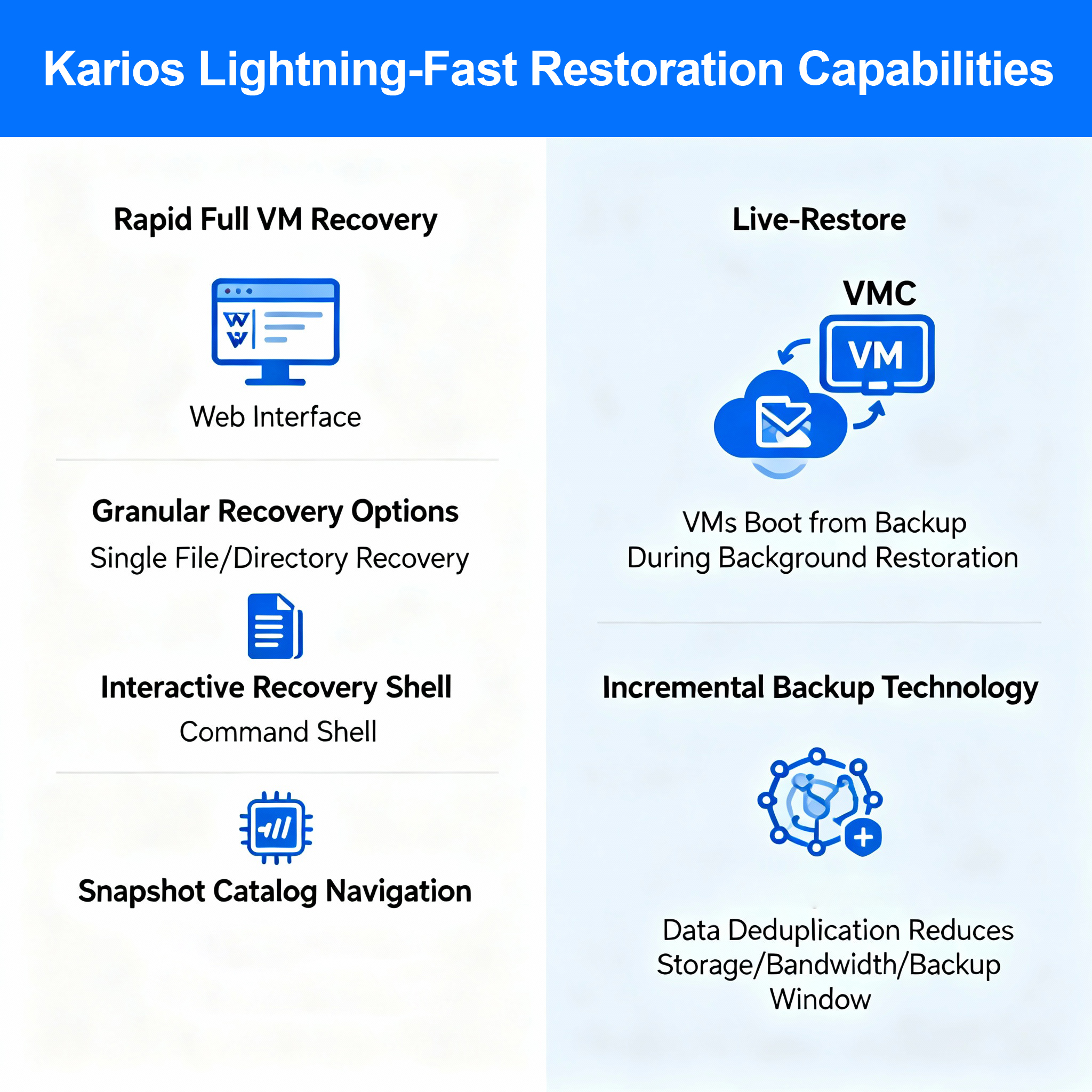
Live-Restore Functionality
An advanced feature enabling virtual machines to boot directly from backup snapshots while restoration proceeds transparently in the background. This capability dramatically reduces Recovery Time Objectives (RTOs) by allowing services to resume operation before complete data restoration is finalized.
Incremental Backup Technology
Backups are transmitted incrementally from protected systems to the Kairos backup infrastructure, where data undergoes deduplication. Since periodic backups typically contain minimal changes, only modified data blocks are read and transmitted, reducing:
- Storage capacity requirements
- Network bandwidth consumption
- Backup window duration
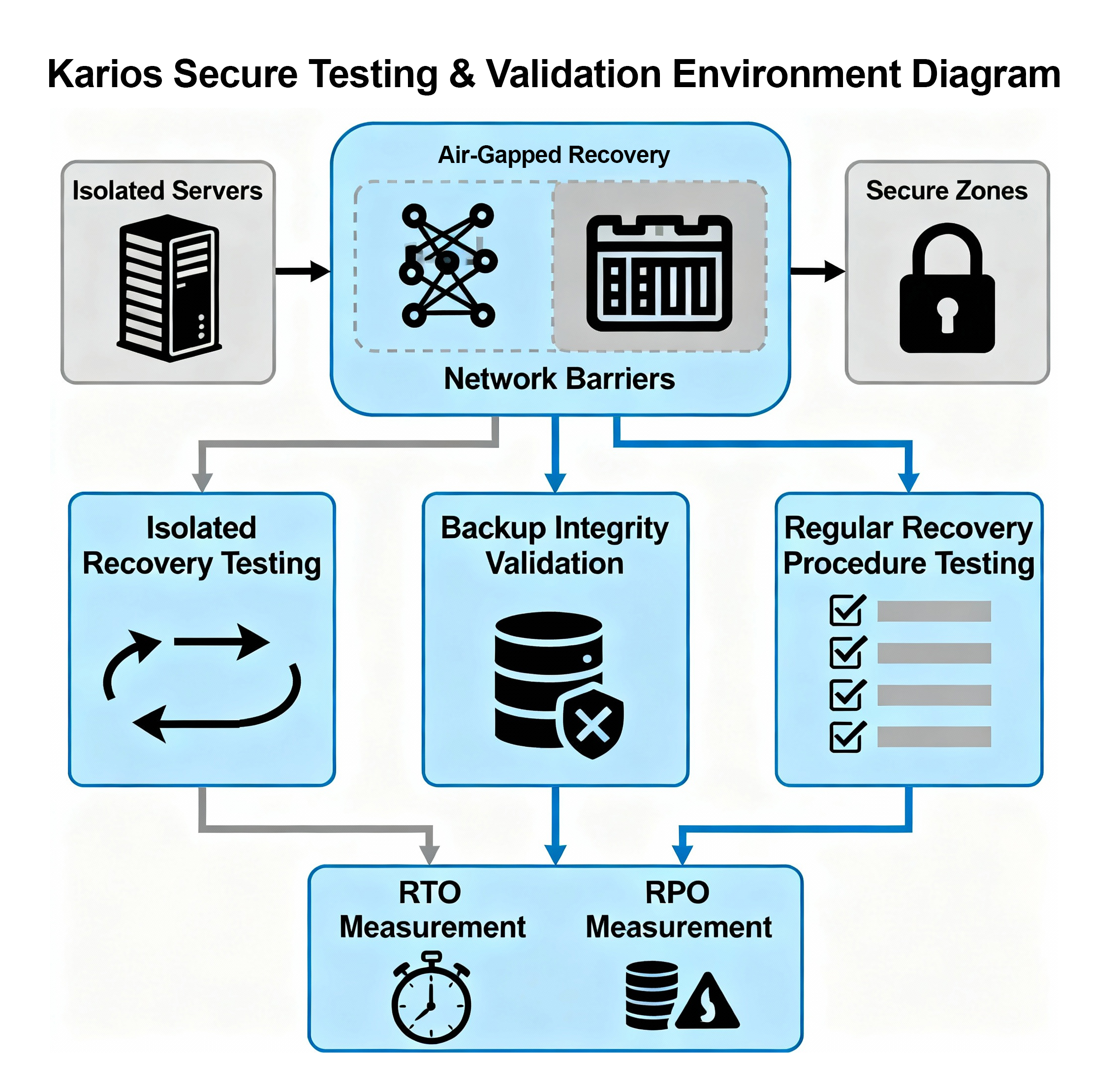
5. Integration with Cleanroom Recovery Architecture
Secure Testing and Validation Environment
Kairos supports integration with cleanroom recovery methodologies, providing isolated environments for secure backup testing and validation without risk to production systems.
Isolated Recovery Testing
Backup integrity can be validated through restoration to segregated network environments, ensuring:
- Recovery procedures are tested regularly without impacting production operations
- Backup data validity is confirmed before disaster scenarios occur
- Recovery time objectives (RTOs) and recovery point objectives (RPOs) are measured and validated
Air-Gapped Recovery Capabilities
The architecture supports deployment of recovery infrastructure in network-isolated segments, preventing lateral movement of threats from compromised production environments to backup systems.
6. Threat Detection and Data Integrity Monitoring: Comprehensive Multi-Layer Protection Architecture
The Kairos disaster recovery platform implements an advanced, multi-layered threat detection and data integrity monitoring system that provides comprehensive protection against ransomware, malware, data corruption, and unauthorized access. Leveraging SeaweedFS’s built-in integrity verification capabilities combined with intelligent behavioral analysis, the solution delivers proactive threat identification while maintaining continuous validation of backup data integrity.

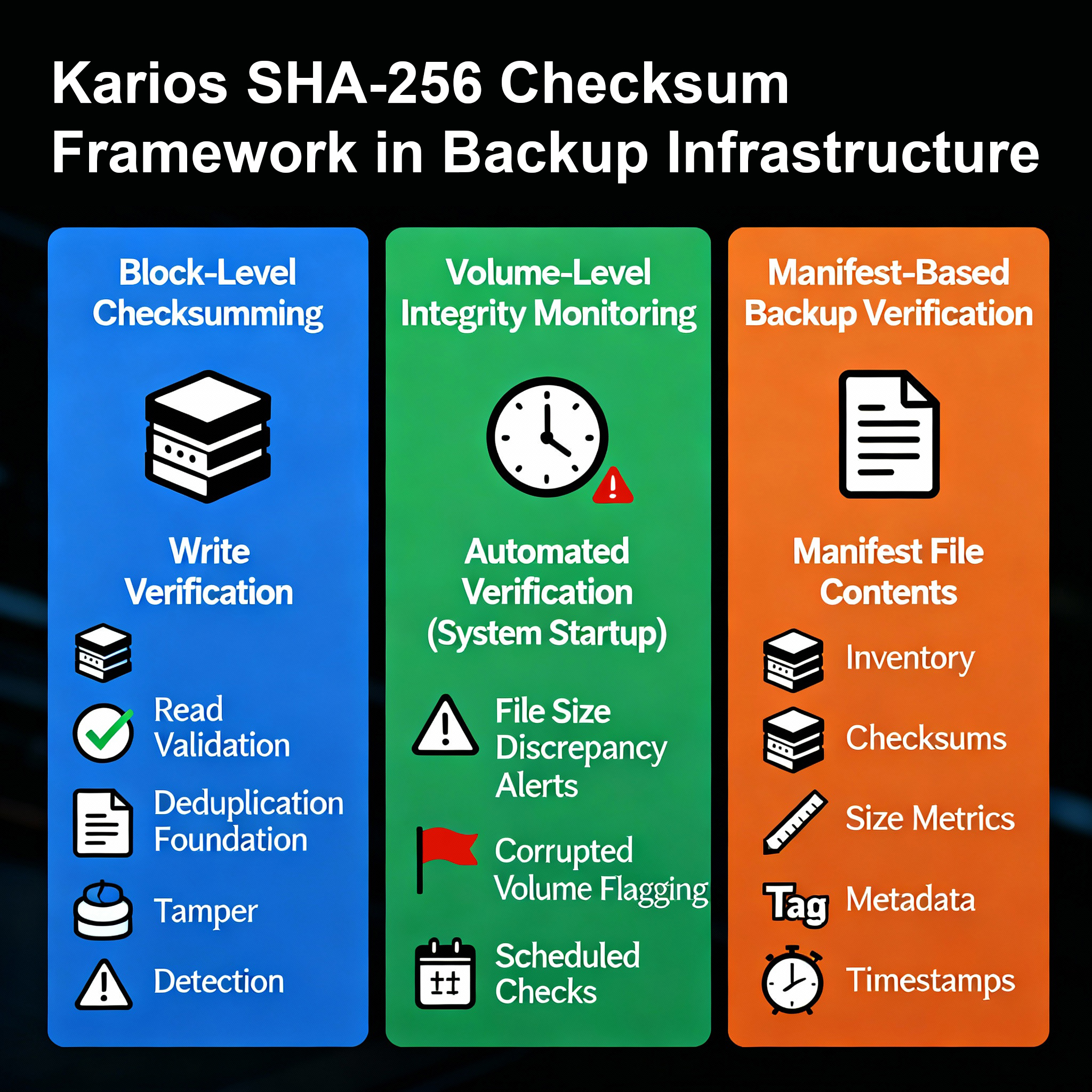
7. Cryptographic Integrity Verification: SHA-256 Checksum-Based Data Validation
The platform employs a comprehensive SHA-256 cryptographic checksumming framework that operates at multiple levels throughout the backup infrastructure:
Block-Level Checksumming
Every data block stored within SeaweedFS receives a unique SHA-256 checksum upon creation. This cryptographic fingerprint serves multiple critical functions:
- Write Verification: Immediately confirms successful storage of data blocks without corruption during the write operation
- Read Validation: Automatically verifies data integrity during retrieval operations, detecting silent data corruption or bit rot
- Deduplication Foundation: Enables content-addressable storage by using checksums as unique identifiers for data blocks
- Tamper Detection: Identifies any unauthorized modification to stored data through checksum mismatches
Volume-Level Integrity Monitoring
SeaweedFS performs automated volume integrity verification during system initialization and on configurable schedules:
- Volume data files are validated against expected checksums stored in metadata structures
- Discrepancies between actual file sizes and expected sizes trigger immediate alerts
- Corrupted volumes are automatically identified and flagged for remediation
- Integrity checks can be scheduled during low-utilization periods to minimize performance impact
Manifest-Based Backup Verification
Each backup operation generates a comprehensive manifest file (index.json format) containing:
- Complete inventory of all files and data blocks included in the backup set
- Individual checksums for every component within the backup
- Total size metrics and metadata attributes
- Timestamp information for audit trail purposes
This manifest enables rapid verification of backup completeness and integrity without requiring full data reads, substantially reducing verification overhead while maintaining rigorous validation standards.
8. Data Compression and Entropy Analysis
Encryption fundamentally alters data characteristics, rendering it incompressible. This property provides a powerful detection mechanism integrated directly into the backup process.
Compression Ratio Baseline Establishment
SeaweedFS utilizes Zstandard (ZSTD) compression for all stored data. Under normal circumstances, most business data achieves compression ratios between 40-70%, depending on file types:
- Document Files: Typically achieve 60-70% compression
- Database Files: Generally achieve 40-60% compression
- Image and Media Files: Already compressed, yielding 0-20% additional compression
- Source Code and Text: Often achieve 70-80% compression
Entropy Monitoring During Backup Operations
When ransomware encrypts files, the resulting ciphertext appears random, exhibiting high entropy characteristics:
- Real-Time Compression Analysis: During backup operations, the system continuously monitors compression effectiveness
- Sudden Compression Failure Detection: Identifies situations where previously compressible data suddenly becomes incompressible, indicating possible encryption
- Percentage Threshold Alerts: Generates warnings when compression efficiency degrades beyond statistically expected ranges
- Data Type Correlation: Considers expected compression characteristics based on file types to reduce false positive alerts
9. Automated Backup Verification Scheduling: Comprehensive Data Integrity Validation Framework
Scheduled Verification Operations
The platform enables administrators to configure automated verification schedules ensuring continuous validation of backup integrity:
Full Verification Scans
- Complete Checksum Validation: Reads and validates SHA-256 checksums for every data block within designated backup sets
- Manifest Cross-Reference: Compares actual stored data against manifest file declarations
- Configurable Frequency: Can be scheduled daily, weekly, monthly, or at custom intervals based on organizational requirements
- Resource-Aware Scheduling: Automatically throttles verification operations during peak usage periods to minimize production impact
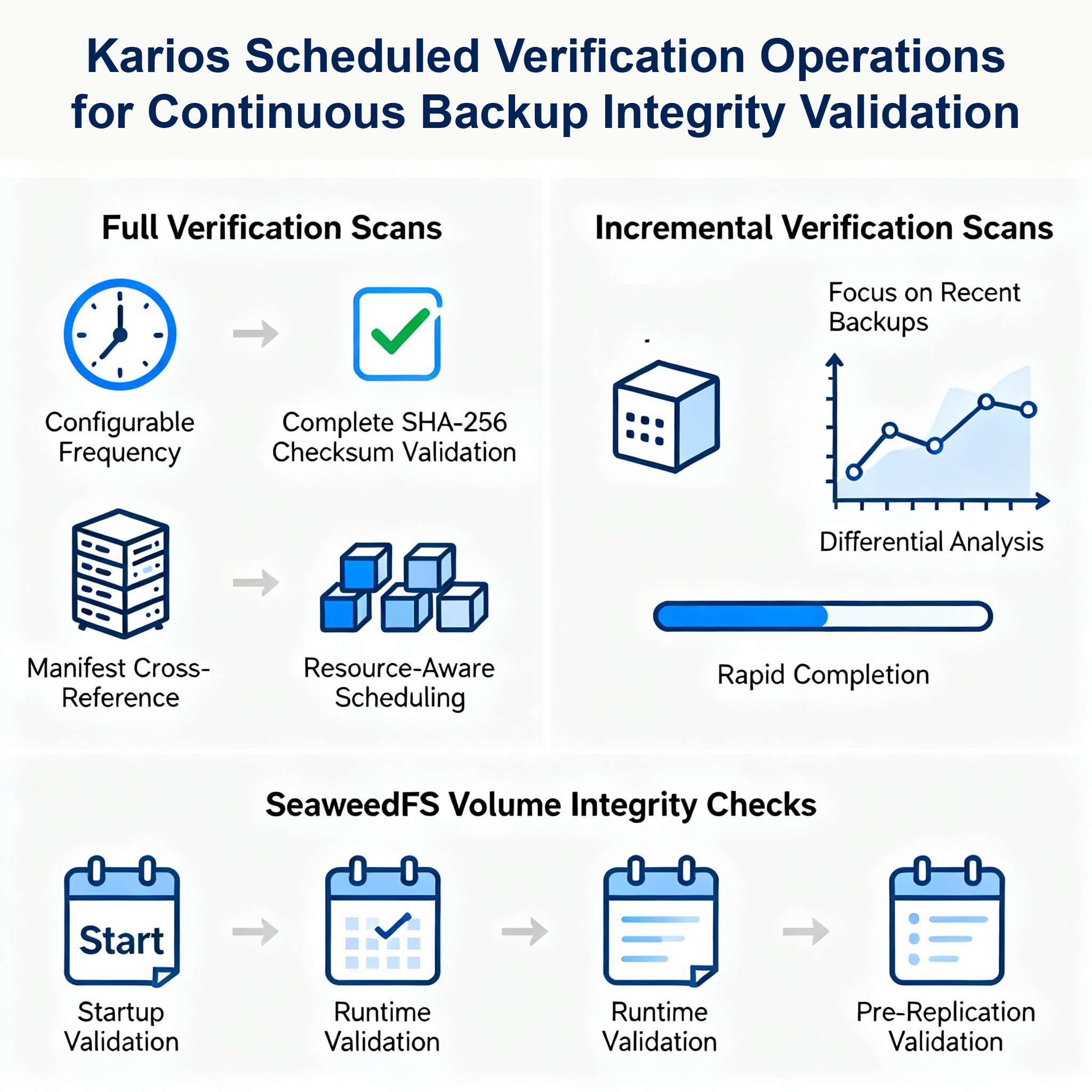
Incremental Verification Scans
- Recent Backup Prioritization: Focuses verification efforts on most recent backup sets where corruption detection provides maximum value
- Differential Analysis: Validates only changed blocks since previous verification operations
- Rapid Completion: Significantly faster than full verification while maintaining high confidence in data integrity
Volume Integrity Checks
SeaweedFS volume servers perform integrity verification at multiple operational stages:
- Startup Verification: Validates volume integrity during system initialization
- Runtime Monitoring: Performs ongoing integrity checks during normal operations
- Pre-Replication Validation: Confirms data integrity before replication to remote sites
10. Immutability and Write-Once-Read-Many (WORM) Protection: Protecting Backups from Ransomware Destruction
Immutable Snapshot Architecture
Backup snapshots are stored with immutable attributes, preventing modification or deletion even by administrative accounts during retention periods:
- Time-Based Immutability: Backup sets cannot be deleted or modified until configured retention periods expire
- Protection Against Compromised Credentials: Even if administrative accounts are compromised, attackers cannot destroy protected backup data
- Compliance Support: Meets regulatory requirements for data retention immutability (SEC 17a-4, FINRA, HIPAA)
SeaweedFS Replication Immutability
Replicated data benefits from additional immutability protections:
- Cross-Data Center Immutability: Replicas in remote locations remain protected even if primary sites are compromised
- Delayed Replication Options: Configurable replication delays ensure clean recovery points exist before malicious changes propagate
- Read-Only Replica Configuration: Secondary sites can be configured as read-only, preventing any modification via compromised network paths
11. Deduplication Layer Security and Validation: Cryptographic Deduplication with Integrity Verification
Content-Addressable Storage Architecture
SeaweedFS implements content-addressable storage where data blocks are identified by cryptographic hashes:
- Checksum as Address: SHA-256 checksums serve as unique identifiers for data blocks
- Collision Resistance: The cryptographic strength of SHA-256 (2^256 possible values) ensures practical impossibility of hash collisions
- Automatic Duplicate Detection: Identical data blocks are automatically identified through checksum matching
- Storage Efficiency: Duplicate blocks are stored only once, dramatically reducing storage capacity requirements
Deduplication Integrity Verification
The deduplication system includes built-in integrity protection:
- Source Verification: Validates that deduplicated blocks match original source data through checksum comparison
- Reference Count Tracking: Maintains accurate reference counts for shared data blocks
- Garbage Collection Safety: Ensures deduplicated blocks are not prematurely removed while valid references exist
- Corruption Isolation: If a shared data block becomes corrupted, the system can identify all affected backups
Performance Benefits
This approach is particularly effective for virtualized environments containing multiple similar virtual machines:
- Operating System Deduplication: Multiple VMs running identical operating systems share common data blocks
- Application Binary Sharing: Common application installations are deduplicated across multiple instances
- Typical Space Savings: Achieves 80-95% storage reduction for environments with substantial data similarity
- Network Efficiency: Only unique data blocks are transmitted during backup and replication operations
Conclusion: Comprehensive Protection of Data
The Kairos disaster recovery solution implements a comprehensive, multi-layered data integrity monitoring framework that provides robust protection against ransomware, malware, and data corruption. By combining cryptographic integrity verification, entropy analysis and immutable snapshot protection, the platform ensures that backup data remains trustworthy and available for recovery operations even in the face of sophisticated cyber-attacks.
The integration of these capabilities directly into the backup workflow, leveraging SeaweedFS’s native features, provides superior detection efficiency compared to standalone security products while minimizing administrative overhead and infrastructure costs. Continuous monitoring, intelligent alerting, and automated response workflows enable rapid threat identification and coordinated incident response, substantially reducing the impact of ransomware attacks on business operations.

 Nov 05,2025
Nov 05,2025 By admin
By admin